In the digital age, businesses are expanding their horizons and reaching customers across the globe. If you’re looking forward to extending your company’s footprint, exploring the reach of corporate connectivity is vital. Among the connectivity options, one solution stands out: eWAN (Enterprise Wide Area Network), a game-changer in corporate connectivity.
Connectivity Layers
Before learning about Enterprise WAN connectivity in detail, let’s explain the difference between layer 2 and layer 3. Layer 2 connectivity operates at the data link layer, primarily concerned with the exchange of data frames between nodes on a network. It’s similar to building bridges between locations, allowing seamless communication within a confined network. This allows the direct connection between two locations.
On the other hand, layer 3 connectivity operates at the network layer, focusing on routing and forwarding data packets across interconnected networks. It’s comparable to constructing highways between all locations, enabling multipoint connectivity across vast distances. One of the benefits of eWAN is its ability to interconnect several locations seamlessly using layer 3.
Layer 3 connectivity often utilizes MPLS (Multiprotocol Label Switching) technology. MPLS is a versatile networking technique that efficiently directs data packets along predefined paths, enhancing performance and enabling traffic engineering. In essence, MPLS assigns labels to data packets, allowing routers to make forwarding decisions based on these labels rather than lengthy IP address lookups. This streamlines network operations and improves overall efficiency.
The Advantages of Enterprise WAN
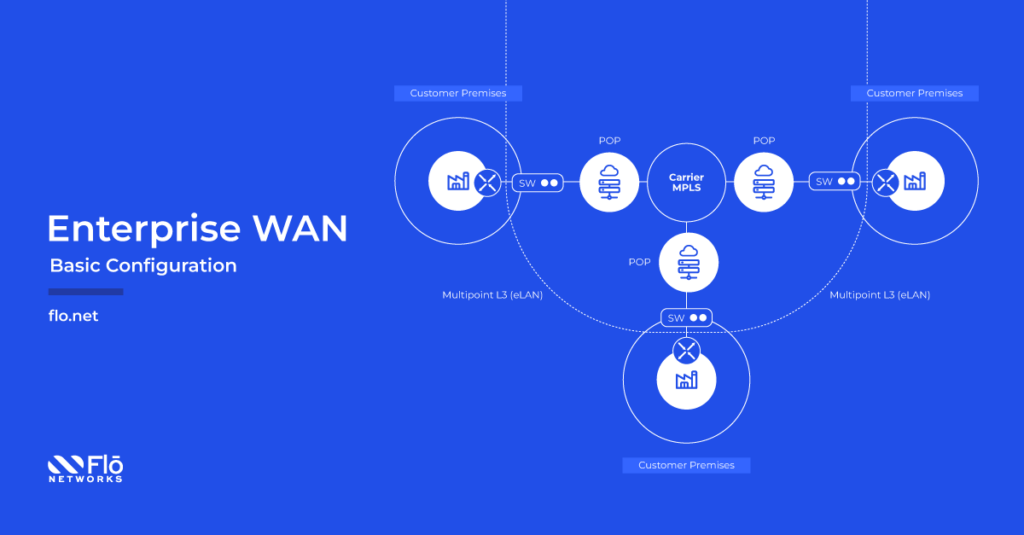
Now, why opt for eWAN over traditional internet-based connections between corporate locations? The answer is in the advantages it offers:
Security: eWAN provides a secure channel for data transmission. Encapsulating data within a private network shields sensitive information, ensuring confidentiality and integrity.
Reliability: With eWAN, each corporate location acts as a synchronized cog, seamlessly interconnected without the hiccups often encountered over the public internet. Say goodbye to latency issues and hello to uninterrupted productivity.
Scalability: As your company expands its footprint, scalability becomes essential. Enterprise WAN offers flexibility and scalability for your network infrastructure effortlessly, accommodating your growing demands without compromising performance or security.
Centralized Management: With a unified control mechanism, you easily gain visibility and control over your entire network landscape, streamlining operations and troubleshooting potential bottlenecks. This is a key advantage over layer 2 point-to-point connections.
Virtual Private Network Capabilities: eWAN brings the power of Virtual Private Networks (VPNs) to the table, ensuring secure communication channels between corporate locations. By leveraging VPN technology, you fortify your network against external threats while enabling seamless data exchange within your private network environment.
Conclusion
In conclusion, eWAN enables communication between branch offices, production facilities, and devices distributed over a wide geographical area, with security, reliability, and scalability. Whether you’re a startup or an enterprise company, embracing the power of eWAN is laying a robust foundation for future growth and success.
Choose Flō Networks as your connectivity partner and join thousands of companies based in the United States and Mexico that interconnect their corporate headquarters, data centers, and cloud services across borders with us. Focus on your business while we take care of the connectivity challenges ahead.

